-
Notifications
You must be signed in to change notification settings - Fork 28.9k
[SPARK-42761][BUILD][K8S] Upgrade kubernetes-client to 6.5.0
#40381
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
|
@dongjoon-hyun FYI |
 dongjoon-hyun
left a comment
dongjoon-hyun
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thank you for pinging me.
fabric8:kubernetes-client to 6.5.0fabric8:kubernetes-client to 6.5.0
 dongjoon-hyun
left a comment
dongjoon-hyun
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
For the record, this looks like a false alarm. I don't think Apache Spark is affected by SnakeYAML issue because fabric8io community also got the confirmation from snakeyml community officially that they are not affected.
Could you double check it, @bjornjorgensen ?
|
If you agree with the above assessment, please remove the misleading CVE information from the PR description, @bjornjorgensen . |
|
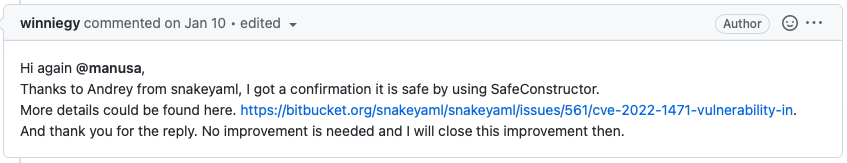
Well, the comment that you are refereeing to, have a link but I cant get in 3 weeks later they merged a PR fabric8io/kubernetes-client@43b04f6 that fix this issue. And yesterday SNYK open a PR to my repo for this issue. bjornjorgensen#102 |
|
The maintainers of the library contend that the application's trust would already have had to be compromised or established and therefore dispute the risk associated with this issue on the basis that there is a high bar for exploitation. Thus, no fix is expected. https://security.snyk.io/vuln/SNYK-JAVA-ORGYAML-3152153 This is part of snakeyaml release notes 2.0 (2023-02-26) Fix #570: SafeConstructor ignores LoaderOptions setCodePointLimit() (thanks to Robert Patrick) Update #565: (Backwards-incompatible) Do not allow global tags by default to fix CVE-2022-1471 (thanks to Jonathan Leitschuh) 1.32 (2022-09-12) Fix #547: Set the limit for incoming data to prevent a CVE report in NIST. By default it is 3MB |
|
@bjornjorgensen . Do you mean you can not trust Hence, the migration happens independently from the CVE. It's just for the future release. In short, the following claim sounds wrong to me according to the context.
|
|
BTW, I have two additional questions for the following PR you referred.
|
|
ok, I didn't know who this user was. I have updated the PR text now. |
|
Now that it turns out that the information that I have been given is not correct. This change the whole picture with why we should include this PR. I think we can wait until we are done with 3.4 so that we are on the safe side. |
 dongjoon-hyun
left a comment
dongjoon-hyun
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thank you for updating, @bjornjorgensen . +1, LGTM for Apache Spark 3.5.0 for now.
Let's merge and test this new dependency together in master branch for a while.
fabric8:kubernetes-client to 6.5.0kubernetes-client to 6.5.0
kubernetes-client to 6.5.0kubernetes-client to 6.5.0
|
Hey @dongjoon-hyun, Will this fix will be backported to other maintained branches (specifically the one I care about is the 3.3 branch)? Thanks! |
|
Line 213 in cd16624
|
|
To @fryz . As @bjornjorgensen mentioned, the answer is no.
|
### What changes were proposed in this pull request? Upgrade fabric8:kubernetes-client from 6.4.1 to 6.5.0 [Release notes](https://github.com/fabric8io/kubernetes-client/releases/tag/v6.5.0) ### Why are the changes needed? ### Does this PR introduce _any_ user-facing change? No. ### How was this patch tested? Pass GA Closes apache#40381 from bjornjorgensen/kub-client6.5.0. Authored-by: bjornjorgensen <[email protected]> Signed-off-by: Dongjoon Hyun <[email protected]>
What changes were proposed in this pull request?
Upgrade fabric8:kubernetes-client from 6.4.1 to 6.5.0
Release notes
Why are the changes needed?
Does this PR introduce any user-facing change?
No.
How was this patch tested?
Pass GA