-
Notifications
You must be signed in to change notification settings - Fork 10.5k
Fix DetectMisplacedLambdaAttribute analyzer and tests #44061
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
c9f7a9b to
ccfd9ab
Compare
|
|
||
| static IMethodSymbol? GetReturnedInvocation(IBlockOperation blockOperation) | ||
| { | ||
| foreach (var op in blockOperation.ChildOperations.Reverse()) |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Why do we search the child operations in reverse here?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I figured it made sense to search from the end of the method for return operations instead of the start because I'd expect most returns to be nearer to the end. Multiple return operations are an edge case this analyzer never really accounted for anyway.
|
I want to manually see if the analyzer is broken in our rc2 nightlies before undrafting this considering this PR targets |
|
There appears to be a real issue with analyzer creating some false positives, but we think it has not been reported because of dotnet/roslyn#63225. Below, the We've noticed that the false positive warning does not always show up in the error list: I've also noticed that our tests run with an outdated version of Microsoft.CodeAnalysis.CSharp compared to VS 17.4.0 Preview 2.0. Our tests run against 4.200.22.12801 and VS 17.4.0 Preview 2.0 loads 4.400.22.43014. Is this expected because it needs to work with 17.3 or something? Are we worried about incompatibilities? @dotnet/aspnet-build @jaredpar @dotnet/minimal-apis What do we think about bringing this to tactics for rc2 or GA? |
|
Hi @halter73. Please make sure you've updated the PR description to use the Shiproom Template. Also, make sure this PR is not marked as a draft and is ready-to-merge. To learn more about how to prepare a servicing PR click here. |
There shouldn't be any incompatibilities I'm aware of. |
|
@dotnet/aspnet-admins This has been approved by tactics. |
 dougbu
left a comment
dougbu
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Undo changes to Build.props please
|
@dougbu The point of the Build.props change was to run the tests that were previously not being run on the CI. This is the most important part of the fix, so I cannot just undo it. I've updated it to only add Microsoft.AspNetCore.App.Analyzers.Test.csproj to Build.props rather than adding all the projects in the AspNetCoreAnalyzers directory since the non-test projects are already included by Microsoft.AspNetCore.App.Ref.csproj. Does this address your concern? |
Yes. I'll enable auto-merge (squash). @SteveSandersonMS |
|
/azp run |
|
Azure Pipelines successfully started running 3 pipeline(s). |
* Fix DetectMisplacedLambdaAttribute analyzer and tests * Add AspNetCoreAnalyzers to Build.props * Update eng/Build.props
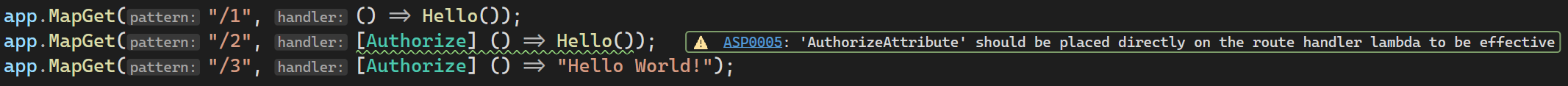
Description
Before this change, we had a whole suite of analyzers that were not being tested on the CI.
I just happened to be looking at these analyzers because we started working on new out-of-band analyzers for the hackathon. When running the tests locally, I discovered failing tests because of a false positive in our
DetectMisplacedLambdaAttributelogic. That's when I realized these tests must not be running on the CI.Customer Impact
Customers haven't noticed this. Below, the
[Authorize]attribute is in the correct location, but we improperly warn anyway.But we've noticed that the false positive warning does not always show up in the error list. It appears to be due to the race condition fixed by dotnet/roslyn#6322. We think this might be why no customers have reported this issue. The false positive happens to be in a fairly specific case where an attribute is added to a lambda that then immediately invokes another method.
Regression?
Tests haven't been running on the CI, so the regression likely happened sometime between preview1 when the analyzer was first released and now.
Risk
I think it would be higher risk to continue running no tests for these analyzers in our
release/7.0branch.Verification
Packaging changes reviewed?